yfrog ‘secret’ email addresses are easy to figure out
yfrog has (had?) a feature to send images to your twitter/yfrog account via MMS or email. This process requires NO password, and it relies on the yfrog email for your account being “secret”.
The email for yfrog is of the form; twitteraccountname.yfrog-generated-word@yfrog.com, basically an attacker knows everything except the “yfrog-generated-word”.
Also note that until earlier today, this generated email was being shown in your page. Why is this a problem? Imagine your gmail page or facebook prominently showing your “password” while you are logged in. Anybody looking over your shoulder could get into your account (here’s an image of the changes yfrog implemented over this).
So how hard is it to crack these emails if you don’t happen to peek at another user, turns out, not very hard at all.
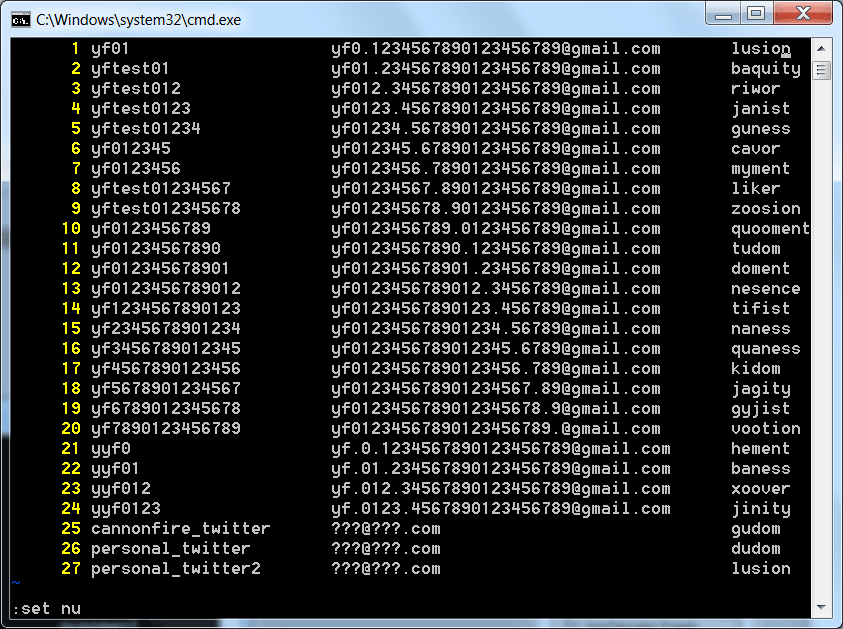
I created several twitter accounts based on the same gmail address, thanks to a feature in gmail that lets you put dots in the name. Since twitter only lets you use 1 email per twitter account, this feature becomes very useful. Here are the results;
I tried 24 fresh new accounts, the last 3 are 2 personal accounts and the test at the cannonfire blog post.
Right off the bat, notice we already have a dupe: “lusion”, which kind of indicates yfrog uses a very simple and small dictionary.
The next interesting generated words are:
* g[udom], d[udom], t[udom]
Which obviously is “udom” with a variation on the first letter.
A common pattern seems to be that there are variations of prefixes and then the last sequences of the word are repeated.
* gu[ness], na[ness], ba[ness]
* my[ment], do[ment], he[ment]
* lu[sion], zoo[sion] (there’s also voot[ion] but maybe that’s another sequence)
* jan[ist], tif[ist], gyj[ist]
* jin[ity], batu[ity], jag[ity]
You see the patterns. We’re either dealing with a static dictionary, or a very simple algorithm that is at least reusing the postfix part of the word. The prefix may also be reused, if it’s randomly putting together strings.
It’s pretty scandalous than an app would use an email address for security, but it’s even worse that said email address is so easily guessed. In my small test of 27, I got 1 repeat and found many repeated substrings. It wouldn’t take much effort for an attacker to do this, specially since he/she just has to send a set of these combinations via email and wait for one to hit.
I hope yfrog permanently turns off this “MMS” feature (which they may have done), in the meantime the best option is to go to your twitter settings->applications and “Revoke Access” to the yfrog application.
Or maybe twitter can do this for all users, this app is dangerous because it’s a big security hole leveraging the twitter API and leading to easy abuse.